hashcat
by hashcat
hashcat is an advanced CPU-based password recovery tool designed to brute-force and dictionary attack password hashes.
Hashcat is a password recovery tool used to recover lost or forgotten passwords. It is an open source tool designed to assist users in recovering their passwords. Hashcat is the most advanced password recovery tool available. It uses a variety of techniques to recover passwords including dictionary attacks, brute force attacks, rainbow tables, and more.
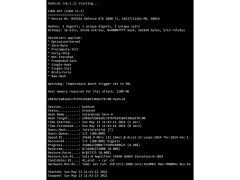
Hashcat provides a powerful suite of features that make it a valuable tool for users who need to recover passwords. Hashcat can be used on both Windows and Linux operating systems. It supports a variety of hash algorithms, including MD5, SHA1, SHA256, SHA512, NTLM, and many more. It is also capable of cracking passwords of any length, making it an ideal tool for recovering long and complex passwords.
Hashcat also offers a wide range of customization options for users. It can be used to generate custom wordlists for dictionary attacks or to set specific rules for brute force attacks. Hashcat also offers a graphical user interface (GUI) which makes it easy to access the features of the tool.
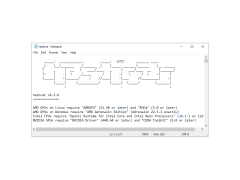
Hashcat also offers extensive support for a variety of graphics processing units (GPUs). This allows users to take advantage of the processing power of GPUs to accelerate the cracking process. Hashcat also offers support for distributed cracking, allowing users to spread the work of cracking passwords across multiple computers.
The main features of Hashcat include:
• Support for numerous hash algorithms
• Ability to crack passwords of any length
• Customizable wordlists and rules for dictionary and brute force attacks
• Graphical user interface
• Support for multiple GPUs
• Distributed cracking support
• Extensive documentation and support
• Open source code available for download
Hashcat provides a powerful suite of features that make it a valuable tool for users who need to recover passwords. Hashcat can be used on both Windows and Linux operating systems. It supports a variety of hash algorithms, including MD5, SHA1, SHA256, SHA512, NTLM, and many more. It is also capable of cracking passwords of any length, making it an ideal tool for recovering long and complex passwords.
Hashcat also offers a wide range of customization options for users. It can be used to generate custom wordlists for dictionary attacks or to set specific rules for brute force attacks. Hashcat also offers a graphical user interface (GUI) which makes it easy to access the features of the tool.
Hashcat also offers extensive support for a variety of graphics processing units (GPUs). This allows users to take advantage of the processing power of GPUs to accelerate the cracking process. Hashcat also offers support for distributed cracking, allowing users to spread the work of cracking passwords across multiple computers.
The main features of Hashcat include:
• Support for numerous hash algorithms
• Ability to crack passwords of any length
• Customizable wordlists and rules for dictionary and brute force attacks
• Graphical user interface
• Support for multiple GPUs
• Distributed cracking support
• Extensive documentation and support
• Open source code available for download
Hashcat enables users to perform highly efficient and accelerated password cracking using advanced methods and techniques.
The minimum hardware requirements for hashcat are:
- A CPU with at least 2 cores
- A minimum of 4GB of RAM
- A graphics card with at least 1GB of dedicated video RAM
The minimum software requirements for hashcat are:
- Linux, macOS, or Windows operating system
- The latest version of hashcat installed
- An internet connection (for downloading the latest version of hashcat)
- A CPU with at least 2 cores
- A minimum of 4GB of RAM
- A graphics card with at least 1GB of dedicated video RAM
The minimum software requirements for hashcat are:
- Linux, macOS, or Windows operating system
- The latest version of hashcat installed
- An internet connection (for downloading the latest version of hashcat)
PROS
Supports a wide variety of hashing algorithms.
Extremely fast password cracking tool.
Highly customizable with flexible attack modes.
Extremely fast password cracking tool.
Highly customizable with flexible attack modes.
CONS
Requires knowledge of command line to operate effectively.
High system hardware requirements for optimal use.
No graphical user interface provided.
High system hardware requirements for optimal use.
No graphical user interface provided.
Muhammad S.
1. Hashcat is a powerful password recovery tool.
2. It is fast, efficient and supports a wide range of algorithms.
3. It has a nice user interface and is easy to use.
4. It has a great online community with plenty of resources.
5. It can be used to crack multiple hashes at once.
6. It supports GPU acceleration to speed up the process.
7. It is also compatible with multiple operating systems.
8. The cost is reasonable compared to the value it provides.
9. It supports the use of wordlists and masks for more advanced attacks.
10. The software is constantly updated with new features and improvements.