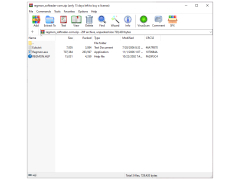
Regmon
by Mark Russinovich
Small but powerful application that shows you real-time changes made to the Windows registry
Regmon is an application that monitors the calls of programs running on your computer to the system registry. It is possible to configure filters to monitor only certain registry keys, and there is a function for logging events.
Regmon allows users to efficiently monitor and filter real-time registry activities for enhanced system security.
Requires Windows operating system
Requires at least 512MB RAM
Requires minimum 100MB free disk space
Supports 32-bit and 64-bit systems
Requires at least 512MB RAM
Requires minimum 100MB free disk space
Supports 32-bit and 64-bit systems
PROS
Allows real-time monitoring for Windows Registry changes.
Offers filters to identify specific registry changes.
It's a freeware tool, low on system resources.
Offers filters to identify specific registry changes.
It's a freeware tool, low on system resources.
CONS
Very complex user interface for beginners.
Does not support real-time monitoring.
Limited compatibility with latest operating systems.
Does not support real-time monitoring.
Limited compatibility with latest operating systems.
Mason
Well I believe this can be accomplished in the system settings, or task management. To download a application only to take of space and force your computer to run a program that will just slow it down seems useless. I am not entirely sure what all the functions of the application are, but I would personally pass on this one.
Blake
Honestly, I have no idea what this software does, but it sounds like it keeps the software secure from Malware or secure from unwanted changes. I don't know anyone personally that can benefit from this, but it definitely sounds like the right product for someone!