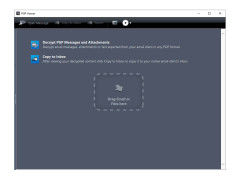
PGP Desktop is one of the most powerful programs for data protection and encryption. It can encrypt business correspondence, email, text information, as well as files and entire hard drives.
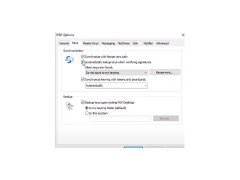
Due to the asymmetric encryption features, it is necessary to first create a key pair consisting of a public and private key, which will then be used for encryption, as well as for installation and verification of digital signatures. Among the main settings you need to specify the encryption and hashing algorithms, the lifetime and length of the key, as well as to enter a passphrase that will be used to access the container with the keys. The program will ask you to do all of this at the first launch.
The main benefit of using PGP Desktop is its ability to provide robust data protection and encryption for files, emails, and entire hard drives.
Once installed, PGP Desktop integrates with Explorer and adds new menu items to the Windows context menu. They can quickly encrypt files or directories. The selected items are placed in an extension container. PGP. By the way, you can activate container compression in the program settings, in this case they will take up less space and get an additional level of protection against cryptanalysis. All container actions are logged, from which the user can get information about who created or opened the encrypted archives at any time.
Among other things, the program can create virtual encrypted disks that can be connected and operated in the same way as regular disks, as well as encrypt partitions and wipe free space, making it impossible to recover deleted data. In addition, after the installation, the PGP Shredder dumpster will appear on the desktop, which is used for permanent deletion: the files placed in it will be deleted and the space occupied by them will be zeroed out.
Despite such a wide range of functions, it is quite easy to work with PGP Desktop, the interface will not cause difficulties in mastering, wizards will help you to perform the basic operations, and in case of any questions there is a deployed help system.
- Secure data encryption with asymmetric algorithms;
- the ability to install and verify digital signatures and use different hashing algorithms;
- convenient tools for key management;
- the ability to exchange files and directories securely;
- logging of all operations with protected containers;
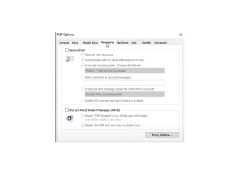
- E-mail encryption, AOL Instant Messenger correspondence, and any text data in open windows;
- Availability of tools for irretrievable data deletion;
- convenient interface, in which all the tools are "arranged" into sections.
PROS
Easy to set up and user-friendly interface.
Supports email, files, and disk encryption.
CONS
Limited support and updates.
May slow down system performance.